Practical mastering IBM MQ basics
SSL/TLS configuration (2)
*This series may be revised based on the latest mqpgf/mqpcf. Please always download and use the latest version.
Issue a certificate at the Certificate Authority (CA) from the created certificate request (CSR)
From the certificate request (CSR) created on each machine, sign with each private CA and issue the certificate.
Make sure that the OPENSSL_CONF environment variable points to openssl.cnf for CA.
You will be asked to enter the pass phrase of the private key of the CA certificate on the way, so enter the pass phrase specified when creating the self-signed root certificate.
Check the displayed contents (the part in blue below), and if there are no mistakes, enter "y" twice.
*The following is an example of Windows, but the same applies to Linux and HPE NonStop.
However, note the difference in the location of openssl.cnf あand the CSR file, and the name of the CSR file.
...\openssl\winca>openssl ca -in C:\ProgramData\IBM\MQ\qmgrs\PL92W\ssl\key.csr Using configuration from ...\openssl\winca\openssl.cnf Enter pass phrase for .../openssl/winca/private/cakey.pem: winca Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Aug 4 06:43:52 2021 GMT Not After : Aug 2 06:43:52 2031 GMT Subject: countryName = JP stateOrProvinceName = Chiba organizationName = Pulsar Integration PL92WA Inc. commonName = www.pulsarintegration.PL92W.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 14:F6:86:73:F7:4A:61:AF:D5:1F:6F:F4:C1:04:02:63:68:8F:F2:2F X509v3 Authority Key Identifier: keyid:23:0B:5D:88:01:02:F5:6E:2B:F7:67:3D:67:A3:EF:AB:72:8D:43:A2 Certificate is to be certified until Aug 2 06:43:52 2031 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Certificate: Data: Version: 3 (0x2) Serial Number: 1 (0x1) Signature Algorithm: sha256WithRSAEncryption Issuer: C=JP, ST=Chiba, O=Pulsar Integration Inc., CN=www.pulsarintegration.com/ emailAddress=support@pulsarintegration.com Validity Not Before: Aug 4 06:43:52 2021 GMT Not After : Aug 2 06:43:52 2031 GMT Subject: C=JP, ST=Chiba, O=Pulsar Integration PL92WA Inc., CN=www.pulsarintegration.PL92W.com Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:db:6b:22:f5:ce:9c:1b:60:04:63:c8:2c:67:3d: .... Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 14:F6:86:73:F7:4A:61:AF:D5:1F:6F:F4:C1:04:02:63:68:8F:F2:2F X509v3 Authority Key Identifier: keyid:23:0B:5D:88:01:02:F5:6E:2B:F7:67:3D:67:A3:EF:AB:72:8D:43:A2 Signature Algorithm: sha256WithRSAEncryption 8b:2d:d0:e9:18:03:8f:e4:ba:66:32:0a:9c:52:e8:5d:87:2a: .... -----BEGIN CERTIFICATE----- MIID+DCCAuCgAwIBAgIBATANBgkqhkiG9w0BAQsFADCBkTELMAkGA1UEBhMCSlAx .... -----END CERTIFICATE----- Data Base Updated
*Option descriptions
ca: Performs basic CA functions and issues X.509 certificates and certificate revocation lists.
-in <filename>: Specify a certificate request (CSR) file.
This example creates a PEM file with the certificate serial number as the filename in the winca/newcerts directory.
dir ...\winca\newcerts .... 2021/08/04 15:44 4,721 01.pem ....
Make sure that the issued certificate information is added to the index.txt file and that the serial number in the serial file is incremented.
...\openssl\winca>type index.txt V 310802064352Z 01 unknown /C=JP/ST=Chiba/O=Pulsar Integration PL92WA Inc. /CN=www.pulsarintegration.PL92W.com ...\openssl\winca>type serial 02
Certificate verification
Here are some command lines that are useful for certificate validation.
About the format of the certificate/key file
This document assumes the PEM(Base64 ascii) format as the certificate/key file format. If you use an external CA and receive a certificate in DER (binary) format from the actual CA, you can convert it to PEM format with the following command.
openssl x509 -in 01.cer -inform der -out 01.pem -outform pem
openssl x509 -in cacert.cer -inform der -out cacert.pem -outform pem
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-in <filename>: File name to read.
-inform der: Input data is in DER format.
-out <filename>: The file name of the data output destination.
-outform pem: Output data is in PEM format.
Check the symmetry of private and public keys
The private key file contains the private key, the CSR, and the server certificate contains the public key.
You can check the symmetry of the private key and public key by comparing the values output when -modulus of the openssl command is specified for these files.
Compare the hash values in each file and make sure they are all the same.
In the case of GSKit(Windows/Linux), the above PEM format private key file is not created.
*The following is an example in the HPE NonStop OSS (Linux equivalent) environment, but the same applies to Windows and Linux.
The location and file name of the corresponding file are different for each platform, so specify them appropriately.
*Private key file(only for HPE NonStop) $ openssl rsa -in PL81Nkey.pem -modulus -noout | openssl md5 Enter pass phrase for PL81Nkey.pem: PL81Npass (stdin)= f23c301e7005e4fd0f48b221e66b09dd *CA signature certificate(server certificate) $ openssl x509 -in 01.pem -modulus -noout | openssl md5 (stdin)= f23c301e7005e4fd0f48b221e66b09dd *Certificate request(CSR)(default file name is key.csr when created with GSKit(Windows/Linux)) $ openssl req -in PL81Nreq.pem -modulus -noout | openssl md5 (stdin)= f23c301e7005e4fd0f48b221e66b09dd
*Option descriptionsrsa: Operate the RSA private key and check its contents.
x509: Create, verify, and perform various other operations on X.509 certificates.
req: You can use this command to create, verify, operate certificate requests.
-in <filename>: File name to read.
-modulus: Output public key method (modulo).
-noout: Suppresses the output of the certificate in encoded form.
md5: Generate a message digest(hash value) using md5.
CA signing certificate and CA certificate subject and issuer check
Check the contents(subject and issuer) of CA-signed certificate (server certificate) and CA (root) certificate. "issuer" is the issuer of the certificate, both with the same CA Distinguished Name.
*CA signature certificate(server certificate) $ openssl x509 -subject -issuer -noout -in 01.pem subject=C = AU, ST = Sydney, O = Pulsar Integration PL81NA Inc., CN = www.sd.pulsarintegration.PL81N.com issuer=C = AU, ST = Sydney, O = Pulsar Integration SD Inc., CN = www.sd.pulsarintegration.com, emailAddress = support@sd.pulsarintegration.com *CA(root) certificate $ openssl x509 -subject -issuer -noout -in cacert.pem subject=C = AU, ST = Sydney, O = Pulsar Integration SD Inc., CN = www.sd.pulsarintegration.com, emailAddress = support@sd.pulsarintegration.com issuer=C = AU, ST = Sydney, O = Pulsar Integration SD Inc., CN = www.sd.pulsarintegration.com, emailAddress = support@sd.pulsarintegration.com
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-subject: Output the certificate owner name.
-issuer: Output the issuer of the certificate.
-in <filename>: File name to read.
-noout: Suppresses the output of the certificate in encoded form.
Verification of intermediate CA certificate or root certificate and server certificate
Verify the validity of the X.509 certificate. It performs a comprehensive check on the certificates and also validates each certificate in the certificate chain.
.../openssl/nsca: openssl verify -CAfile cacert.pem newcerts/01.pem newcerts/01.pem: OK *It should be displayed as OK
*Option descriptions
verify: Verify the validity of the X.509 certificate.
Comprehensive checks are performed on the certificates, including validation on each certificate in the certificate chain.
-CAfile <filename1>: Specify the name of the trusted certificate file.
<filename2>: Specify the file name of the CA signing certificate to be verified.
Check the contents of the server certificate
Check that the expiration date and other contents of the server certificate are as expected.
openssl x509 -noout -text -in newcerts/01.pem
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-noout: Suppresses the output of the certificate in encoded form.
-text: View the certificate in a readable format.
-in <filename>: File name to read.
Add CA(root) certificate to key repository(GSKit)
For Windows and Linux, it is necessary to store the certificate in the key repository. Note that there is no intermediate certificate in this example, but all certificates must be stored in the order of the certificate chain starting with the root certificate.
Go to the repository location and copy the root certificate to the repository location.
*The root certificate can be in any location.
*For Windows >cd C:\ProgramData\IBM\MQ\qmgrs\PL92W\ssl >copy .../openssl/winca/cacert.pem cacert_win.pem *For Linux $ cd /var/mqm/qmgrs/PL91L/ssl $ cp -p ..../openssl/lnxca/cacert.pem cacert_lnx.pem
Add the certificate to the key repository using the runmqckm command.
The label names for CA(root) and personal certificates must be unique.
*The following is an example of Windows, but the same applies to Linux.
...\ssl>runmqckm -cert -add -db key.kdb -pw PL92Wpass -label PLWCA -file cacert_win.pem -format ascii 5724-H72 (C) Copyright IBM Corp. 1994, 2020. >
*Option descriptions
-cert: The target of the command is the certificate.
-add: Add CA certificate.
-db filename: Specify the fully qualified file name of the CMS key database.
-pw password: Specify the password for the CMS key database.
-label labelname: The label name to add to the certificate.
-file filename: The name of the certificate file.
-format ascii: Certificate format.
Specify Base64-encoded ASCII.
If the certificates used on both sending and receiving channels are signed by different CAs, then each key repository must contain both CA certificates.
In this example, different CAs were created for Windows, Linux, and HPE NonStop, so obtain the CA certificate created on the machine you plan to connect to by ftp, etc, and follow the same procedure as above to add it to the key repository.
Here we are adding the CA certificate on the HPE NonStop that we plan to connect to.
*Since the PEM format CA certificate is in ASCII format, the FTP transfer mode can be transferred using Ascii, but binary mode is also acceptable.
...\ssl>runmqckm -cert -add -db key.kdb -pw PL92Wpass -label PLNCA -file cacert_ns.pem -format ascii 5724-H72 (C) Copyright IBM Corp. 1994, 2020. >
Check the added certificate on the key repository.
First, list the stored certificates.
...\ssl>runmqckm -cert -list -db key.kdb -pw PL92Wpass 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Certificates in database C:\ProgramData\IBM\MQ\qmgrs\PL92W\ssl\key.kdb: PLNCA PLWCA >
*Option descriptions
-cert: The target of the command is the certificate.
-list: List the certificates in the key database.
-db filename: Specify the fully qualified file name of the CMS key database.
-pw password: Specify the password for the CMS key database.
Next, display the details of each stored certificate.
...\ssl>runmqckm -cert -details -label PLWCA -db key.kdb -pw PL92Wpass 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Label: PLWCA Key Size(E): 2048 Version(V): X509 V3 Serial Number: 78 8C A6 A9 32 69 37 D5 AA D6 74 40 A1 29 B4 2F CE 2D 99 36 Issued by: EMAILADDRESS=support@pulsarintegration.com, CN=www.pulsarintegration.com, O=Pulsar Integration Inc., ST=Chiba, C=JP Subject: EMAILADDRESS=support@pulsarintegration.com, CN=www.pulsarintegration.com, O=Pulsar Integration Inc., ST=Chiba, C=JP Valid: From: Friday, July 16, 2021 1:14:26 PM JST To: Monday, July 14, 2031 1:14:26 PM JST Fingerprint: SHA1: D5:AC:62:6E:2C:AB:CA:62:98:B9:23:96:3C:AA:21:C0:9C:87:9A:80 SHA256: C4:48:E1:C0:4C:43:C3:F9:05:2A:DD:A7:D2:BC:0B:9A:F0:A4:3A:88:22:8A:32:99:DB:02:CB: 6D:F8:E6:29:83 HPKP: hZlIRTwboAC7MN6xcWY6yikcW8eB2JH/q2OW1MClDZs= Extentions: - AuthorityKeyIdentifier: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 23 0b 5d 88 01 02 f5 6e 2b f7 67 3d 67 a3 ef ab .......n..g.g... 0010: 72 8d 43 a2 r.C. ] ] - SubjectKeyIdentifier: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 23 0b 5d 88 01 02 f5 6e 2b f7 67 3d 67 a3 ef ab .......n..g.g... 0010: 72 8d 43 a2 r.C. ] ] - BasicConstraints: ObjectId: 2.5.29.19 Criticality=true BasicConstraints:[ CA:true PathLen:2147483647 ] Signature Algorithm(S): SHA256withRSA (1.2.840.113549.1.1.11) Trust Status: enabled >
*Option descriptions
-cert: The target of the command is the certificate.
-details: View specific certificate details.
-label labelname: The label name of the certificate.
-db filename: Specify the fully qualified file name of the CMS key database.
-pw password: Specify the password for the CMS key database.
...\ssl>runmqckm -cert -details -label PLNCA -db key.kdb -pw PL92Wpass 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Label: PLNCA Key Size(E): 2048 Version(V): X509 V3 Serial Number: 4B C2 81 70 AA 2F B4 81 07 42 45 61 CE 70 68 57 FF 58 0E F5 Issued by: EMAILADDRESS=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com, O=Pulsar Integration SD Inc., ST=Sydney, C=AU Subject: EMAILADDRESS=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com, O=Pulsar Integration SD Inc., ST=Sydney, C=AU Valid: From: Friday, July 16, 2021 5:12:20 PM JST To: Monday, July 14, 2031 5:12:20 PM JST Fingerprint: SHA1: AF:AA:6D:B8:41:2D:56:9D:B0:B7:35:08:4C:A7:2D:8E:62:D7:0C:1E SHA256: 80:50:3B:A9:21:88:0C:E9:BE:A9:9F:C5:A7:D9:8E:5F:67:0C:4E:A1:CC:4C:97:09:FD:C8:65: 45:BC:EF:8B:44 HPKP: dyYgV54de+jSLni8STO+6MTnWBrHloammUlzTWXUICY= Extensions: - AuthorityKeyIdentifier: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: d4 b7 9b 1a 4a 4c f1 a0 3c 3d f0 94 2d 7c 9f ca ....JL.......... 0010: 40 1d 1a eb .... ] ] - SubjectKeyIdentifier: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: d4 b7 9b 1a 4a 4c f1 a0 3c 3d f0 94 2d 7c 9f ca ....JL.......... 0010: 40 1d 1a eb .... ] ] - BasicConstraints: ObjectId: 2.5.29.19 Criticality=true BasicConstraints:[ CA:true PathLen:2147483647 ] Signature Algorithm(S): SHA256withRSA (1.2.840.113549.1.1.11) Trust Status: enabled >
Receive personal certificate to key repository(GSKit)
Add a CA-signed certificate(personal certificate) to the key repository for each queue manager. This is the work to be done for Windows and Linux. Importing a personal certificate must always be in the key repository that created the CSR.
Copy the CA-signed personal certificate(CA-signed certificate) to the location of the repository.
*The CA signature certificate can be placed anywhere.
*For Windows >cd C:\ProgramData\IBM\MQ\qmgrs\PL92W\ssl >copy .../openssl/winca/newcerts/01.pem PL92WA.pem *For Linux $ cd /var/mqm/qmgrs/PL91L/ssl $ cp -p ..../openssl/lnxca/newcerts/01.pem PL91LA.pem
Add the personal certificate using the runmqckm command.
*The following is an example of Windows, but the same applies to Linux.
...\ssl>runmqckm -cert -receive -file PL92WA.pem -db key.kdb -pw PL92Wpass -format ascii 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Validation successful. >
*Option descriptions
-cert: The target of the command is the certificate.
-receive: Receive certificate.
-file filename: The name of the certificate file.
-db filename: Specify the fully qualified file name of the CMS key database.
-pw password: Specify the password for the CMS key database.
-format ascii: Certificate format.
Specify Base64-encoded ASCII.
Check the CA signing certificate you added on the key repository.
The label name of the personal certificate (CA signature certificate) specified when creating the CSR will be displayed in the list of stored certificates.
...\ssl>runmqckm -cert -list -db key.kdb -pw PL92Wpass 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Certificates in database C:\ProgramData\IBM\MQ\qmgrs\PL92W\ssl\key.kdb 内の証明書: PL92WA PLNCA PLWCA >
Also check the contents of the personal certificate(CA signature certificate).
...\ssl>runmqckm -cert -details -label PL92WA -db key.kdb -pw PL92Wpass 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Label: PL92WA Key Size(E): 2048 Version(V): X509 V3 Serial Number: 01 Issued by: EMAILADDRESS=support@pulsarintegration.com, CN=www.pulsarintegration.com, O=Pulsar Integration Inc., ST=Chiba, C=JP Subject: CN=www.pulsarintegration.PL92W.com, O=Pulsar Integration PL92WA Inc., ST=Chiba, C=JP Valid: From: Wednesday, August 4, 2021 3:43:52 PM JST To: Saturday, August 2, 2031 3:43:52 PM JST Fingerprint: SHA1: 92:86:14:20:45:E3:99:E6:3C:DC:0C:38:25:FF:73:94:2E:74:E1:10 SHA256: CB:22:A5:A0:08:39:A0:A3:91:1E:C0:F7:CF:BC:61:A4:6C:EB:18:3F:30:05:CA:AD:A9:6C:C6: 27:2B:C2:90:0A HPKP: 4O3ZNADha0Lu4/lDO/8fm7q8uuVUWj9k1sOllWDB4ew= Extentions: - AuthorityKeyIdentifier: ObjectId: 2.5.29.35 Criticality=false AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 23 0b 5d 88 01 02 f5 6e 2b f7 67 3d 67 a3 ef ab .......n..g.g... 0010: 72 8d 43 a2 r.C. ] ] - SubjectKeyIdentifier: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 14 f6 86 73 f7 4a 61 af d5 1f 6f f4 c1 04 02 63 ...s.Ja...o....c 0010: 68 8f f2 2f h... ] ] - BasicConstraints: ObjectId: 2.5.29.19 Criticality=false BasicConstraints:[ CA:false PathLen: undefined ] Signature Algorithm(S): SHA256withRSA (1.2.840.113549.1.1.11) Trust Status: enabled >
Creating and deploying SSL/TLS related files(Openssl)
HPE NosStop does not have a key repository like GSKit. Place the related file created by the specified procedure in the location specified by the SSLKEYR attribute of the queue manager.
Concatenate the CA-signed server certificate and key file
Combine the CA-signed server certificate and key file into one file as follows.
The label name specified for CERTLABL of HPE NonStop is the part excluding the extension of the server certificate.
In the example below, "PL81NA" is specified as CERTLABL.
$ pwd .../openssl/nsca/PL81N $ cp -p ../newcerts/01.pem . $ cat 01.pem PL81Nkey.pem > PL81NA.pem
We will also verify the combined files just in case.
$ openssl x509 -subject -issuer -noout -in PL81NA.pem subject=C = AU, ST = Sydney, O = Pulsar Integration PL81NA Inc., CN = www.sd.pulsarintegration.PL81N.com issuer=C = AU, ST = Sydney, O = Pulsar Integration SD Inc., CN = www.sd.pulsarintegration.com, emailAddress = support@sd.pulsarintegration.com
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-subject: Output the certificate owner name.
-issuer: Output the issuer of the certificate.
-in <filename>: File name to read.
-noout: Suppresses the output of the certificate in encoded form.
$ openssl verify -CAfile ../cacert.pem PL81NA.pem PL81NA.pem: OK
*Option descriptions
verify: Verify the validity of the X.509 certificate.
Comprehensive checks are performed on the certificates, including validation on each certificate in the certificate chain.
-CAfile <filename1>: Specify the name of the trusted certificate file.
<filename2>: Specify the file name of the CA signing certificate to be verified.
Combine all CA certificates used for SSL/TLS communication
If the root certificate, intermediate certificate, and certificate used for both sending and receiving channels are signed by different CAs, combine all those CA certificates.
Transfer CA certificates on Windows, Linux machines and combine them with CA certificates on HPE NonStop.
$ pwd .../openssl/nsca/PL81N $ cp -p ../cacert.pem cacert_ns.pem $ ls -l cacert*.pem ... 1468 Aug 10 11:48 cacert_lnx.pem ... 1476 Jul 16 17:12 cacert_ns.pem ... 1456 Aug 10 11:41 cacert_win.pem $ cat cacert_ns.pem cacert_win.pem cacert_lnx.pem > trust.pem $ ls -l trust.pem ... 4400 Aug 10 11:49 trust.pem
Creating a path/phrase stash file
Create a pass phrase storage (stash) file using the amqrsslc command provided by MQ for HPE NonStop.
To create a pass phrase stash file of the private key of the certificate store PL81NA.pem will be as follows.
You will be prompted to enter the pass phrase along the way, so enter the passphrase you specified when you created the certificate request (CSR).
Alternatively, echo it to the command line.
*Do not specify the extension ".pem" for the "-s" parameter.
$ amqrsslc -s PL81NA Enter password for Keystore PL81NA : PL81Npass Stashed the password in file PL81NA.sth or $ echo PL81Npass | amqrsslc -s PL81NA Stashed the password in file PL81NA.sth $ ls -l *.sth .... 128 Aug 10 13:30 PL81NA.sth
*Option descriptions
-s : Key store path
Place created files in the SSLKey repository
Check the queue manager's SSLKEYR property for the location of the key repository.
Note that even when using CERTLABL, the receiving MCA(amqrmppa) will read "cert.pem" and "Stash.sth" or the server certificate specified in the queue manager attribute CERTLABL by default for non-TLS SSL channels(CERTLABL and SNI cannot be used) at initialization.
Therefore, it is also necessary to place the file with the name of "cert.pem" and "Stash.sth".
Even when using CERTLABL, the receiving channel will fail to start if "cert.pem" and "Stash.sth" are not located on the receiving channel side.
Here, cert.pem and Stash.sth uses a copy of PL81NA.pem and PL81NA.sth.
$ mqpcf qmgr -qm PL81N SSLKEYR 1: QMNAME(PL81N) SSLKEYR(.../var/mqm/qmgrs/PL81N/ssl)
*Option descriptions
qmgr: Display queue manager properties.
SSLKEYR : Show only SSLKEYR and mandatory properties
$ cp -p PL81NA.pem <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ $ cp -p PL81NA.sth <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ $ cp -p trust.pem <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ $ cp -p PL81NA.pem <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/cert.pem $ cp -p PL81NA.sth <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/Stash.sth *Check the file permissions and confirm that the MQM group has R/W permissions. cd <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ $ chmod 666 * <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl: ls -l total 35 -rw-rw-rw- 1 MQM.MANAGER MQM 6526 Aug 10 11:10 PL81NA.pem -rw-rw-rw- 1 MQM.MANAGER MQM 128 Aug 10 13:30 PL81NA.sth -rw-rw-rw- 1 MQM.MANAGER MQM 128 Aug 10 13:30 Stash.sth -rw-rw-rw- 1 MQM.MANAGER MQM 6526 Aug 10 11:10 cert.pem -rw-rw-rw- 1 MQM.MANAGER MQM 4400 Aug 10 11:49 trust.pem
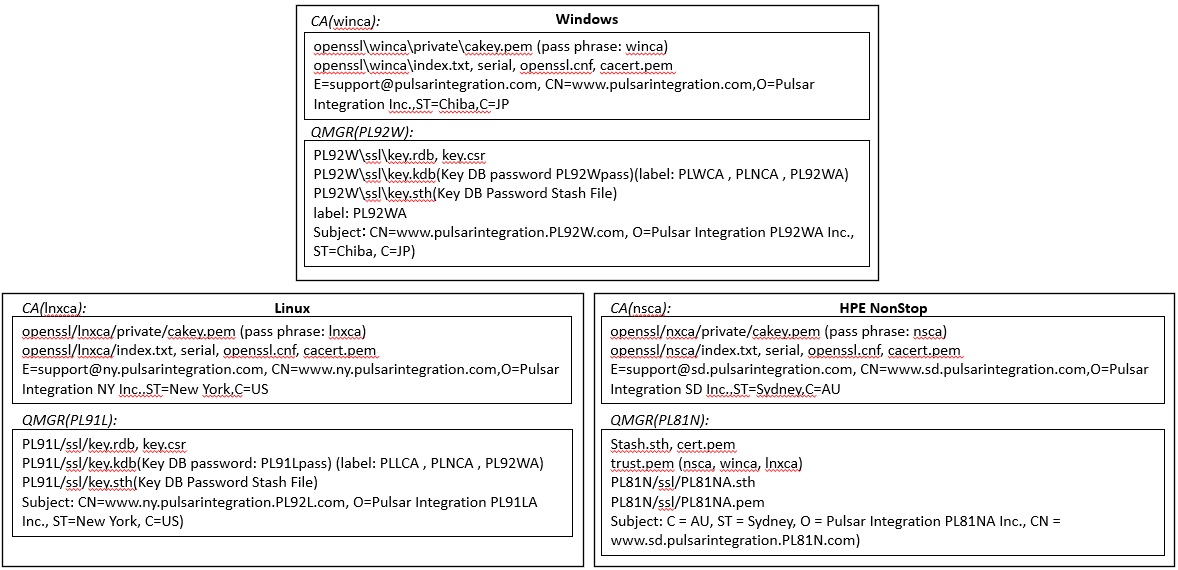
Testing connections between queue managers using TLS
Since it is assumed that CERTLABL/SNI will be used, it is necessary to specify a "TLS" CipherSpec. Use TLS_RSA_WITH_AES_256_CBC_SHA256 as an example. To define a TLS channel, simply specify CipherSpec in the channel property sslciph and the certificate label in certlabl(if needed). The same CipherSpec must be specified for the send and receive channels. Also, for the same reason that HPE NonStop (Openssl) required a file with the name "cert.pem"/"Stash.sth", the label "ibmwebspheremq<qmgr name>" specified in CERTLABL of the Windows/Linux(GSKit) queue manager property is referenced as the default label. Therefore, change it to the same label specified for CERTLABL of the channel. Otherwise, as with HPE NonStop (Openssl), the receiving channel will display an error and the TLS connection will fail. If you change the properties of the channel, such as CERTLABL or CipherSpec, restart the channel. If you change the SSL/TLS certificate file or Key repository, you need to execute "refresh security type (ssl)" or restart the queue manager.
Creating a TLS connection definition
Below is a sample TLS connection definition on each machine between Windows and HPE NonStop and between HPE NonStop and Linux. (The same applies when connecting between Windows and Linux.)
*Windows <-> HPE NonStop [ Windows ] <Change CERTLABL for queue manager> >mqpcf mqsc -qm PL92W -s "dis qmgr CERTLABL" 1: AMQ8408I: QMNAME(PL92W) CERTLABL(ibmwebspheremqpl92w) >mqpcf mqsc -qm PL92W -s "alter qmgr certlabl(PL92WA)" alter qmgr certlabl(PL92WA) 3 : alter qmgr certlabl(PL92WA) 1: AMQ8005I: >mqpcf mqsc -qm PL92W -s "dis qmgr CERTLABL" 1: AMQ8408I: QMNAME(PL92W) CERTLABL(PL92WA) >mqpcf mqsc -qm PL92W -s "refresh security type(ssl)" 1: AMQ8560I: <Sender side channel(SDR)> >mqpcf mqsc -qm PL92W -s "def ql(PL81N) usage(xmitq)" >mqpcf mqsc -qm PL92W -s "def chl(PL92W.PL81N) chltype(sdr) conname('<hostname or ipaddr> (<port>)') xmitq(PL81N) certlabl(PL92WA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" >mqpcf sta -qm PL92W -c PL92W.PL81N <Receiver side channel(RCVR)> >mqpcf mqsc -qm PL92W -s "def listener(listener) trptype(tcp) port(<port>) control(qmgr)" >mqpcf stalsn -qm PL92W -ln LISTENER >mqpcf lsst -qm PL92W -ln LISTENER >mqpcf mqsc -qm PL92W -s "def chl(PL81N.PL92W) chltype(rcvr) certlabl(PL92WA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" [ HPE NonStop ] <Sender side channel(SDR)> $ mqpcf mqsc -qm PL81N -s "refresh security type(ssl)" $ mqpcf mqsc -qm PL81N -s "def ql(PL92W) usage(xmitq)" $ mqpcf mqsc -qm PL81N -s "def chl(PL81N.PL92W) chltype(sdr) conname('<hostname or ipaddr> (<port>)') xmitq(PL92W) certlabl(PL81NA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" $ mqpcf sta -qm PL81N -c PL81N.PL92W <Receiver side channel(RCVR)> $ mqpcf mqsc -qm PL81N -s "def listener(listener) trptype(tcp) port(<port>) control(qmgr)" $ mqpcf stalsn -qm PL81N -ln LISTENER $ mqpcf lsst -qm PL81N -ln LISTENER $ mqpcf mqsc -qm PL81N -s "def chl(PL92W.PL81N) chltype(rcvr) certlabl(PL81NA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" ※ HPE NonStop <-> Linux [ HPE NonStop ] <Sender side channel(SDR)> $ mqpcf mqsc -qm PL81N -s "def ql(PL91L) usage(xmitq)" $ mqpcf mqsc -qm PL81N -s "def chl(PL81N.PL91L) chltype(sdr) conname('<hostname or ipaddr> (<port>)') locladdr('<hostname or ipaddr>/<tcpip process>) xmitq(PL91L) certlabl(PL81NA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" $ mqpcf sta -qm PL81N -c PL81N.PL91L $ mqpcf chs -qm PL81N -c PL81N.PL91L <Receiver side channel(RCVR)> $ mqpcf mqsc -qm PL81N -s "def listener(listener2) trptype(tcp) port(<port>) ipaddr('<hostname or ipaddr>/\$<tcpip process>') control(qmgr)" $ mqpcf stalsn -qm PL81N -ln LISTENER2 $ mqpcf lsst -qm PL81N -ln LISTENER2 $ mqpcf mqsc -qm PL81N -s "def chl(PL91L.PL81N) chltype(rcvr) certlabl(PL81NA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" [ Linux ] <Change CERTLABL for queue manager> $ mqpcf mqsc -qm PL91L -s "dis qmgr CERTLABL" 1: AMQ8408I: Display Queue Manager details. QMNAME(PL91L) CERTLABL(ibmwebspheremqpl91l) $ mqpcf mqsc -qm PL91L -s "alter qmgr certlabl(PL91LA)" $ mqpcf mqsc -qm PL91L -s "refresh security type(ssl)" <Sender side channel(SDR)> $ mqpcf mqsc -qm PL91L -s "def ql(PL81N) usage(xmitq)" $ mqpcf mqsc -qm PL91L -s "def chl(PL91L.PL81N) chltype(sdr) conname('<hostname or ipaddr> (<port>)') xmitq(PL81N) certlabl(PL91LA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)" $ mqpcf sta -qm PL91L -c PL91L.PL81N $ mqpcf chs -qm PL91L -c PL91L.PL81N <Receiver side channel(RCVR)> $ mqpcf mqsc -qm PL91L -s "def listener(listener) trptype(tcp) port(<port>) control(qmgr)" $ mqpcf stalsn -qm PL91L -ln LISTENER $ mqpcf lsst -qm PL91L -ln LISTENER $ mqpcf mqsc -qm PL91L -s "def chl(PL81N.PL91L) chltype(rcvr) certlabl(PL91LA) sslciph(TLS_RSA_WITH_AES_256_CBC_SHA256)"
Checking TLS connection results
Check the connection result in the channel status properties. Below is a description of typical properties. The Distinguished Name (DN) of the opposite side is displayed in SSLPEER.
| SECPROT |
Defines the security protocol currently in use and set automatically, based on the value you set for SSLCIPH.
The values to be set are as follows.
|
||||||||
| SSLCERTI | The full Distinguished Name of the issuer(CA) of the remote certificate. | ||||||||
| SSLPEER | Distinguished Name of the peer queue manager or client at the other end of the channel. It also includes the remote partner's certificate serial number (SERIALNUMBER attribute). |
※ Windows -> HPE NonStop [ Windows ] >mqpcf chs -qm PL92W -c PL92W.PL81N SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL92W.PL81N) CHLTYPE(SDR) CONNAME(xxx.xxx.xxx.xxx(xxxx)) CHLINSTYPE(CURRENT) RQMNAME(PL81N) SECPROT(TLSV12) SSLCERTI(E=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com,O=Pulsar Integration SD Inc.,ST=Sydney,C=AU) SSLPEER(SERIALNUMBER=01,CN=www.sd.pulsarintegration.PL81N.com, O=Pulsar Integration PL81NA Inc.,ST=Sydney,C=AU) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(MQGET) XMITQ(PL81N) [ HPE NonStop ] $ mqpcf chs -qm PL81N -c PL92W.PL81N SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL92W.PL81N) CHLTYPE(RCVR) CONNAME(xxx.xxx.xxx.xxx) CHLINSTYPE(CURRENT) RQMNAME(PL92W) SECPROT(TLSV12) SSLCERTI(E=support@pulsarintegration.com, CN=www.pulsarintegration.com,O=Pulsar Integration Inc.,ST=Chiba,C=JP) SSLPEER(SERIALNUMBER=01,CN=www.pulsarintegration.PL92W.com, O=Pulsar Integration PL92WA Inc.,ST=Chiba,C=JP) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE) ※ HPE NonStop -> Windows [ HPE NonStop ] $ mqpcf chs -qm PL81N -c PL81N.PL92W SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL92W) CHLTYPE(SDR) CONNAME(xxx.xxx.xxx.xxx(xxxx)) CHLINSTYPE(CURRENT) RQMNAME(PL92W) SECPROT(TLSV12) SSLCERTI(E=support@pulsarintegration.com, CN=www.pulsarintegration.com,O=Pulsar Integration Inc.,ST=Chiba,C=JP) SSLPEER(SERIALNUMBER=01, CN=www.pulsarintegration.PL92W.com,O=Pulsar Integration PL92WA Inc.,ST=Chiba,C=JP) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(MQGET) XMITQ(PL92W) [ Windows ] >mqpcf chs -qm PL92W -c PL81N.PL92W SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL92W) CHLTYPE(RCVR) CONNAME(xxx.xxx.xxx.xxx) CHLINSTYPE(CURRENT) RQMNAME(PL81N) SECPROT(TLSV12) SSLCERTI(E=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com,O=Pulsar Integration SD Inc.,ST=Sydney,C=AU) SSLPEER(SERIALNUMBER=01,CN=www.sd.pulsarintegration.PL81N.com, O=Pulsar Integration PL81NA Inc.,ST=Sydney,C=AU) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE) ※ Linux -> HPE NonStop [ Linux ] $ mqpcf chs -qm PL91L -c PL91L.PL81N SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL91L.PL81N) CHLTYPE(SDR) CONNAME(xxx.xxx.xxx.xxx(xxxx)) CHLINSTYPE(CURRENT) RQMNAME(PL81N) SECPROT(TLSV12) SSLCERTI(E=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com,O=Pulsar Integration SD Inc.,ST=Sydney,C=AU) SSLPEER(SERIALNUMBER=01,CN=www.sd.pulsarintegration.PL81N.com, O=Pulsar Integration PL81NA Inc.,ST=Sydney,C=AU) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(MQGET) XMITQ(PL81N) [ HPE NonStop ] $ mqpcf chs -qm PL81N -c PL91L.PL81N SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL91L.PL81N) CHLTYPE(RCVR) CONNAME(xxx.xxx.xxx.xxx) CHLINSTYPE(CURRENT) RQMNAME(PL91L) SECPROT(TLSV12) SSLCERTI(E=support@ny.pulsarintegration.com, CN=www.ny.pulsarintegration.com,O=Pulsar Integration NY Inc.,ST=New York,C=US) SSLPEER(SERIALNUMBER=01,CN=www.ny.pulsarintegration.PL92L.com, O=Pulsar Integration PL91LA Inc.,ST=New York,C=US) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE) ※ HPE NonStop -> Linux [ HPE NonStop ] $ mqpcf chs -qm PL81N -c PL81N.PL91L SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL91L) CHLTYPE(SDR) CONNAME(xxx.xxx.xxx.xxx(xxxx)) CHLINSTYPE(CURRENT) RQMNAME(PL91L) SECPROT(TLSV12) SSLCERTI(E=support@ny.pulsarintegration.com, CN=www.ny.pulsarintegration.com,O=Pulsar Integration NY Inc.,ST=New York,C=US) SSLPEER(SERIALNUMBER=01,CN=www.ny.pulsarintegration.PL92L.com, O=Pulsar Integration PL91LA Inc.,ST=New York,C=US) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(MQGET) XMITQ(PL91L) [ Linux ] $ mqpcf chs -qm PL91L -c PL81N.PL91L SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL91L) CHLTYPE(RCVR) CONNAME(xxx.xxx.xxx.xxx) CHLINSTYPE(CURRENT) RQMNAME(PL81N) SECPROT(TLSV12) SSLCERTI(E=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com,O=Pulsar Integration SD Inc.,ST=Sydney,C=AU) SSLPEER(SERIALNUMBER=01,CN=www.sd.pulsarintegration.PL81N.com, O=Pulsar Integration PL81NA Inc.,ST=Sydney,C=AU) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE)
Enabling deprecated CipherSpecs
You may need to use SSL V3 or the deprecated TLS V1, such as when you need to connect to an older MQ version.
If you need to enable the deprecated CipherSpec, use the following method to enable it.
*CipherSpecs that can be used by default and the method of enabling deprecated CipherSpecs may differ depending on each version and platform of MQ.
Please refer to the documentation of each edition for details.
Enabling deprecated TLS CipherSpecs
Specify the CipherSpec you want to use to the environment variable AMQ_SSL_WEAK_CIPHER_ENABLE or AllowWeakCipherSpec in the SSL stanza of qm.ini.
AMQ_SSL_WEAK_CIPHER_ENABLE environment variable
AMQ_SSL_WEAK_CIPHER_ENABLE=ECDHE_RA_RC4_128_SHA256
AllowWeakCipherSpec parameter of the qm.ini SSL stanza
SSL:
AllowWeakCipherSpec=ECDHE_RA_RC4_128_SHA256
Enabling deprecated SSL CipherSpecs
In addition to specifying the CipherSpec you want to use to the environment variable AMQ_SSL_WEAK_CIPHER_ENABLE or AllowWeakCipherSpec in the qm.ini SSL stanza, you must set AllowSSLV3 = Y in the SSL stanza of qm.ini or set the environment variable AMQ_SSL_V3_ENABLE = 1.
AMQ_SSL_V3_ENABLE=1 and AMQ_SSL_WEAK_CIPHER_ENABLE environment variable
AMQ_SSL_V3_ENABLE=1
AMQ_SSL_WEAK_CIPHER_ENABLE=RC4_MD5_US
AllowSSLV3 = Y and AllowWeakCipherSpec in SSL stanzas in qm.ini
SSL:
AllowSSLV3=Y
AllowWeakCipherSpec=RC4_MD5_US
Enabling deprecated TLSv1 CipherSpecs
In addition to specifying the CipherSpec you want to use to the environment variable AMQ_TLS_WEAK_CIPHER_ENABLE or AllowWeakCipherSpec in the qm.ini SSL stanza, you must set AllowTLSV1 = Y in the SSL stanza of qm.ini or set the environment variable AMQ_TLS_V1_ENABLE = 1.
Environment variables AMQ_SSL_V3_ENABLE = 1 and AMQ_TLS_WEAK_CIPHER_ENABLE
AMQ_TLS_V1_ENABLE=1
AMQ_TLS_WEAK_CIPHER_ENABLE=TLS_RSA_WITH_AES_128_CBC_SHA
AllowTLSV1 = Y and AllowWeakCipherSpec for SSL stanzas in qm.ini
SSL:
AllowTLSV1=Y
AllowWeakCipherSpec=TLS_RSA_WITH_AES_128_CBC_SHA
Channel connection using SSL V3 CipherSpec
Define a channel using the SSL V3 CipherSpec RC4_MD5_US.
*HPE NonStop -> Windows [ Windows/HPE NonStop ] SSL: AllowSSLV3=Yes AllowWeakCipherSpec=RC4_MD5_US #AllowTLSV13=TRUE * In qm.ini on the receiving side (Windows side in this test), if you do not comment out AllowTLSV13 = TRUE, AMQ9616E will be output on the receiving side and the connection will fail. The AMQ9616E error message states that TLS 1.3 and deprecated CipherSpecs cannot be used at the same time. ---- AMQ9616E: The CipherSpec 'RC4_MD5_US' proposed by remote host 'xxx.xxx.xxx.xxx' is not enabled. Explanation The SSL or TLS subsystem at the server end of a channel been configured in such a way that it has rejected the CipherSpec proposed by an SSL or TLS client. This error most commonly occurs when the choice of acceptable CipherSpecs has been limited in one of the following ways: . .... (g) Once you have enabled TLS 1.3, you cannot connect to the queue manager using certain deprecated CipherSpecs, even if it is enabled in the queue manager configuration. For example, SSL v3, RC4 ciphers, and ciphers with less than 112 encryption bits are rejected. To resolve this, either disable TLS 1.3 or use CipherSpec, which is not blocked by TLS 1.3. ---- *If you do not change qm.ini before specifying the deprecated CipherSpec in the channel definition, the following error will occur when defining the channel. MQSC > alter chl(PL81N.PL92W.2) chltype(sdr) SSLCIPH(RC4_MD5_US) 1 : alter chl(PL81N.PL92W.2) chltype(sdr) SSLCIPH(RC4_MD5_US) AMQ8242: SSLCIPH definition wrong. *After changing the SSL stanza of qm.ini, execute "refresh security" or restart the queue manager. [ HPE NonStop ] $ mqpcf mqsc -qm PL81N -s "refresh security type(ssl)" [ Windows ] *In this test, on Windows(reception side), "refresh security" was not enough, and restarting the queue manager was needed. [ Windows ] >mqpcf mqsc -qm PL92W -s "def chl(PL81N.PL92W.2) chltype(rcvr) SSLCIPH(RC4_MD5_US)" [ HPE NonStop ] $ mqpcf mqsc -qm PL81N -s "def ql(PL92W2) usage(xmitq)" $ mqpcf mqsc -qm PL81N -s "def chl(PL81N.PL92W.2) chltype(sdr) conname('xxx.xxx.xxx.xxx(xxxx)') xmitq(PL92W2) SSLCIPH(RC4_MD5_US)" [ HPE NonStop ] $ mqpcf sta -qm PL81N -c PL81N.PL92W.2 $ mqpcf chs -qm PL81N -c PL81N.PL92W.2 SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL92W.2) CHLTYPE(SDR) CONNAME(xxx.xxx.xxx.xxx(xxxx)) CHLINSTYPE(CURRENT) RQMNAME(PL92W) SECPROT(SSLV3) SSLCERTI(E=support@pulsarintegration.com, CN=www.pulsarintegration.com,O=Pulsar Integration Inc.,ST=Chiba,C=JP) SSLPEER(SERIALNUMBER=01, CN=www.pulsarintegration.PL92W.com,O=Pulsar Integration PL92WA Inc.,ST=Chiba,C=JP) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(MQGET) XMITQ(PL92W2) [ Windows ] >mqpcf chs -qm PL92W -c PL81N.PL92W.2 SECPROT SSLCERTI SSLPEER 1: CHANNEL(PL81N.PL92W.2) CHLTYPE(RCVR) CONNAME(xxx.xxx.xxx.xxx) CHLINSTYPE(CURRENT) RQMNAME(PL81N) SECPROT(SSLV3) SSLCERTI(E=support@sd.pulsarintegration.com, CN=www.sd.pulsarintegration.com,O=Pulsar Integration SD Inc.,ST=Sydney,C=AU) SSLPEER(SERIALNUMBER=01,CN=www.sd.pulsarintegration.PL81N.com, O=Pulsar Integration PL81NA Inc.,ST=Sydney,C=AU) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE)
Please note that the detailed restrictions and configuration procedures for enabling the deprecated CipherSpec are expected to vary depending on the MQ edition and CipherSpec.