Practical mastering IBM MQ basics
SSL/TLS configuration (4) elliptic curve
*This series may be revised based on the latest mqpgf/mqpcf. Please always download and use the latest version.
When using SSL/TLS, once you decide on a CipherSpec, you need to prepare a digital certificate (server certificate) that is compatible with that CipherSpec. There are three main types of digital certificates.
| CipherSpec Name Prefix | Required public key type | Digital signature encryption algorithm | Secret key establishment method | |
| Type 1 | ECDHE_ECDSA_ | Elliptic Curve | ECDSA | ECDHE |
| Type 2 | ECDHE_RSA_ | RSA | RSA | ECDHE |
| Type 3 |
(All others) |
RSA | RSA | RSA |
In this verification work, we created an intranet CA and created an RSA public key/self-signed CA(root) certificate, which can be used as is for all types. The server(CA signed) certificate was created with an RSA public key/RSA signature. This type of certificate can be used with Type 2 and Type 3 of the above CipherSpecs types, where both the "public key" and "digital signature encryption algorithm" are RSA. In order to use Type1 CipherSpec, it is necessary to prepare a certificate whose "public key" type is "elliptic curve" and "digital signature encryption algorithm" is "ECDSA".
In this article, we will explain the work procedure when using Type 1 CipherSpec. Except for the method of creating a certificate request, the procedure is almost the same as before, so detailed explanation is omitted, so please refer to the previous explanation if necessary. The following is an example of a client connection, but the idea is basically the same for a server-to-server connection.
Creating a CSR to use Type 1 CipherSpec (GSKit)
If you have never performed the procedure for using SSL/TLS in the client connection up to the previous time, perform the procedure up to just before "Create Certificate Signing Request(CSR) (Windows, Linux)" in "SSL/TLS setup on the client (to create CSR) (GSKit)".
To use Type 1 CipherSpec (ECDHE_ECDSA_ *), you must create a certificate request with the Elliptic Curve ECDSA signing algorithm specified for "-sig_alg" in the runmqakm command.
Here, try using EC_ecdsa_with_SHA512.
For the elliptic curve algorithm, the possible key size values are 256, 384, or 512, and the default elliptic curve key size depends on the signing algorithm: 256 for SHA256, 384 for SHA384, and 512 for SHA512.
If any other key size is specified, GSKKM_ERR_CRYPTO_UNSUPPORTED_MODULUS_SIZE will occur and CSR creation will fail.
*The following is an example of Windows, but the same applies to Linux, and it is specified in one line.
For DN, specify the contents for each server.
...\clientssl>runmqakm -certreq -create -db key.kdb -pw PL921WCpass -label PL921WCB -dn "CN=www.pulsarintegration.PL921WCec.com,O=Pulsar Integration PL921WC Inc.,S=Chiba,C=JP" -size 512 -file key.csr -sig_alg EC_ecdsa_with_SHA512 5724-H72 (C) Copyright IBM Corp. 1994, 2020.
*Option descriptions
-certreq: The target of the command is a certificate request
-create: Create a certificate request
-db filename: Specifies the fully qualified file name of a CMS key database.
-pw password: Specifies the password for the CMS key database.
-label label: Specifies the key label attached to the certificate.
The label is either the value of the CERTLABL attribute, if it is set, or the default ibmwebspheremq with the name of the queue manager all in lowercase.
-dn: distinguished_name: Specifies the X.500 distinguished name enclosed in double quotation marks.
At least one attribute is required.
-size key_size: Specifies the key size.
-file filename: Specifies the file name for the certificate request.
-sig_alg hashalgorithm: Specifies the hashing algorithm used during the creation of a certificate request.
This hashing algorithm is used to create the signature associated with the newly created certificate request.
Make sure that the certificate request is created as expected.
...\clientssl>runmqckm -certreq -details -label PL921WCB -db key.kdb ... A password is required to access the source key database. Please enter a password: PL921WCpass Label: PL921WCA Key Size:522 Subject: CN=www.pulsarintegration.PL921WCec.com, O=Pulsar Integration PL921WC Inc., ST=Chiba, C=JP Fingerprint: 50:7E:85:04:07:A7:2F:65:52:0D:71:56:D4:A5:BB:21 Signature Algorithm: SHA512withECDSA (1.2.840.10045.4.3.4)
*Option descriptions
-certreq: The target of the command is a certificate request
-detail: Show the details of a specific certificate request
-label label: Specifies the key label attached to the certificate.
-db filename: Specifies the fully qualified file name of a CMS key database.
*The Key Size is displayed as 522, but to be exact, there is no size of 512 for the elliptic curve, so there is no problem. Even if you omit the specification of "-size 512", if you specify EC_ecdsa_with_SHA512, the Key Size will be 522 by default.
Creating a CSR to use Type 1 CipherSpec (Openssl)
For Openssl, the procedure for creating a CSR is quite different from RSA. For HPE NonStop, follow the steps described here.
Checking the elliptic curves available in Openssl
First, check the elliptic curves available in your version of Openssl.$ openssl ecparam -list_curves secp112r1 : SECG/WTLS curve over a 112 bit prime field secp112r2 : SECG curve over a 112 bit prime field secp128r1 : SECG curve over a 128 bit prime field secp128r2 : SECG curve over a 128 bit prime field secp160k1 : SECG curve over a 160 bit prime field secp160r1 : SECG curve over a 160 bit prime field secp160r2 : SECG/WTLS curve over a 160 bit prime field secp192k1 : SECG curve over a 192 bit prime field secp224k1 : SECG curve over a 224 bit prime field secp224r1 : NIST/SECG curve over a 224 bit prime field secp256k1 : SECG curve over a 256 bit prime field secp384r1 : NIST/SECG curve over a 384 bit prime field secp521r1 : NIST/SECG curve over a 521 bit prime field prime192v1: NIST/X9.62/SECG curve over a 192 bit prime field prime192v2: X9.62 curve over a 192 bit prime field prime192v3: X9.62 curve over a 192 bit prime field prime239v1: X9.62 curve over a 239 bit prime field prime239v2: X9.62 curve over a 239 bit prime field prime239v3: X9.62 curve over a 239 bit prime field prime256v1: X9.62/SECG curve over a 256 bit prime field sect113r1 : SECG curve over a 113 bit binary field sect113r2 : SECG curve over a 113 bit binary field sect131r1 : SECG/WTLS curve over a 131 bit binary field sect131r2 : SECG curve over a 131 bit binary field sect163k1 : NIST/SECG/WTLS curve over a 163 bit binary field sect163r1 : SECG curve over a 163 bit binary field sect163r2 : NIST/SECG curve over a 163 bit binary field sect193r1 : SECG curve over a 193 bit binary field sect193r2 : SECG curve over a 193 bit binary field sect233k1 : NIST/SECG/WTLS curve over a 233 bit binary field sect233r1 : NIST/SECG/WTLS curve over a 233 bit binary field sect239k1 : SECG curve over a 239 bit binary field sect283k1 : NIST/SECG curve over a 283 bit binary field sect283r1 : NIST/SECG curve over a 283 bit binary field sect409k1 : NIST/SECG curve over a 409 bit binary field sect409r1 : NIST/SECG curve over a 409 bit binary field sect571k1 : NIST/SECG curve over a 571 bit binary field sect571r1 : NIST/SECG curve over a 571 bit binary field c2pnb163v1: X9.62 curve over a 163 bit binary field c2pnb163v2: X9.62 curve over a 163 bit binary field c2pnb163v3: X9.62 curve over a 163 bit binary field c2pnb176v1: X9.62 curve over a 176 bit binary field c2tnb191v1: X9.62 curve over a 191 bit binary field c2tnb191v2: X9.62 curve over a 191 bit binary field c2tnb191v3: X9.62 curve over a 191 bit binary field c2pnb208w1: X9.62 curve over a 208 bit binary field c2tnb239v1: X9.62 curve over a 239 bit binary field c2tnb239v2: X9.62 curve over a 239 bit binary field c2tnb239v3: X9.62 curve over a 239 bit binary field c2pnb272w1: X9.62 curve over a 272 bit binary field c2pnb304w1: X9.62 curve over a 304 bit binary field c2tnb359v1: X9.62 curve over a 359 bit binary field c2pnb368w1: X9.62 curve over a 368 bit binary field c2tnb431r1: X9.62 curve over a 431 bit binary field wap-wsg-idm-ecid-wtls1: WTLS curve over a 113 bit binary field wap-wsg-idm-ecid-wtls3: NIST/SECG/WTLS curve over a 163 bit binary field wap-wsg-idm-ecid-wtls4: SECG curve over a 113 bit binary field wap-wsg-idm-ecid-wtls5: X9.62 curve over a 163 bit binary field wap-wsg-idm-ecid-wtls6: SECG/WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls7: SECG/WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls8: WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls9: WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls10: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls11: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls12: WTLS curve over a 224 bit prime field Oakley-EC2N-3: IPSec/IKE/Oakley curve #3 over a 155 bit binary field. Not suitable for ECDSA. Questionable extension field! Oakley-EC2N-4: IPSec/IKE/Oakley curve #4 over a 185 bit binary field. Not suitable for ECDSA. Questionable extension field! brainpoolP160r1: RFC 5639 curve over a 160 bit prime field brainpoolP160t1: RFC 5639 curve over a 160 bit prime field brainpoolP192r1: RFC 5639 curve over a 192 bit prime field brainpoolP192t1: RFC 5639 curve over a 192 bit prime field brainpoolP224r1: RFC 5639 curve over a 224 bit prime field brainpoolP224t1: RFC 5639 curve over a 224 bit prime field brainpoolP256r1: RFC 5639 curve over a 256 bit prime field brainpoolP256t1: RFC 5639 curve over a 256 bit prime field brainpoolP320r1: RFC 5639 curve over a 320 bit prime field brainpoolP320t1: RFC 5639 curve over a 320 bit prime field brainpoolP384r1: RFC 5639 curve over a 384 bit prime field brainpoolP384t1: RFC 5639 curve over a 384 bit prime field brainpoolP512r1: RFC 5639 curve over a 512 bit prime field brainpoolP512t1: RFC 5639 curve over a 512 bit prime field SM2 : SM2 curve over a 256 bit prime field
*Option descriptions
ecparam: Elliptic curve parameter related operations
-list_curves: Show available elliptic curves.
Creating a private key for an elliptic curve certificate
We will leave the detailed explanation of the displayed elliptic curve cryptography to others, but here use prime256v1 to create a private key for the elliptic curve certificate. Just like when we created the server certificate, I'm working on creating a directory named PL81N_C under .../openssl/nsca. There is no fixed method for this work, so feel free to decide and work at your convenience.
$ cd ..../openssl/nsca $ mkdir PL81N_C $ cd PL81N_C $ openssl ecparam -genkey -name prime256v1 -out ecdsa.key $ ls -l total 1 -rw------- 1 ... 302 Aug 26 13:18 PL81Nec.key
*Option descriptions
ecparam: Elliptic curve parameter related operations
-genkey: Elliptic curve key generation
-name val: specify the elliptic curve parameters to use
-out outfile: File name to output the elliptic curve key
Check the private key you created.
$ openssl ec -in ecdsa.key -text -noout read EC key Private-Key: (256 bit) priv: b6:3c:2e:b3:37:c3:41:ca:8a:a2:68:4c:8f:dc:3d: ea:80:47:38:8d:92:b1:9a:51:71:2c:c0:f7:2c:09: 27:f2 pub: 04:7f:09:47:e9:84:6e:b8:5f:7c:85:15:36:5b:a2: 46:9e:e5:e8:04:14:1e:00:d9:d1:f4:7c:d6:9a:d9: 22:08:11:b8:fe:72:de:89:a2:53:31:91:95:40:19: 99:2a:b8:c7:0b:6b:a1:0b:47:3f:ea:59:66:cd:2c: 6f:29:87:36:ce ASN1 OID: prime256v1 NIST CURVE: P-256
*Option descriptions
ec: Elliptic curve related operations
-in filename: Specifies the elliptic curve key file name.
-text: Converts the read file to a readable format and outputs it.
-noout: Suppresses the output of key files in encoded format.
Set a pass phrase for the private key
Shows the encoding algorithms that can be used when adding a passphrase to a private key.
$ openssl enc -ciphers Supported ciphers: -aes-128-cbc -aes-128-cfb -aes-128-cfb1 -aes-128-cfb8 -aes-128-ctr -aes-128-ecb -aes-128-ofb -aes-192-cbc -aes-192-cfb -aes-192-cfb1 -aes-192-cfb8 -aes-192-ctr -aes-192-ecb -aes-192-ofb -aes-256-cbc -aes-256-cfb -aes-256-cfb1 -aes-256-cfb8 -aes-256-ctr -aes-256-ecb -aes-256-ofb -aes128 -aes128-wrap -aes192 -aes192-wrap -aes256 -aes256-wrap -aria-128-cbc -aria-128-cfb -aria-128-cfb1 -aria-128-cfb8 -aria-128-ctr -aria-128-ecb -aria-128-ofb -aria-192-cbc -aria-192-cfb -aria-192-cfb1 -aria-192-cfb8 -aria-192-ctr -aria-192-ecb -aria-192-ofb -aria-256-cbc -aria-256-cfb -aria-256-cfb1 -aria-256-cfb8 -aria-256-ctr -aria-256-ecb -aria-256-ofb -aria128 -aria192 -aria256 -bf -bf-cbc -bf-cfb -bf-ecb -bf-ofb -blowfish -camellia-128-cbc -camellia-128-cfb -camellia-128-cfb1 -camellia-128-cfb8 -camellia-128-ctr -camellia-128-ecb -camellia-128-ofb -camellia-192-cbc -camellia-192-cfb -camellia-192-cfb1 -camellia-192-cfb8 -camellia-192-ctr -camellia-192-ecb -camellia-192-ofb -camellia-256-cbc -camellia-256-cfb -camellia-256-cfb1 -camellia-256-cfb8 -camellia-256-ctr -camellia-256-ecb -camellia-256-ofb -camellia128 -camellia192 -camellia256 -cast -cast-cbc -cast5-cbc -cast5-cfb -cast5-ecb -cast5-ofb -chacha20 -des -des-cbc -des-cfb -des-cfb1 -des-cfb8 -des-ecb -des-ede -des-ede-cbc -des-ede-cfb -des-ede-ecb -des-ede-ofb -des-ede3 -des-ede3-cbc -des-ede3-cfb -des-ede3-cfb1 -des-ede3-cfb8 -des-ede3-ecb -des-ede3-ofb -des-ofb -des3 -des3-wrap -desx -desx-cbc -id-aes128-wrap -id-aes128-wrap-pad -id-aes192-wrap -id-aes192-wrap-pad -id-aes256-wrap -id-aes256-wrap-pad -id-smime-alg-CMS3DESwrap -idea -idea-cbc -idea-cfb -idea-ecb -idea-ofb -rc2 -rc2-128 -rc2-40 -rc2-40-cbc -rc2-64 -rc2-64-cbc -rc2-cbc -rc2-cfb -rc2-ecb -rc2-ofb -rc4 -rc4-40 -seed -seed-cbc -seed-cfb -seed-ecb -seed-ofb -sm4 -sm4-cbc -sm4-cfb -sm4-ctr -sm4-ecb -sm4-ofb
*Option description
enc: Implementation of encryption or compounding using common key encryption method, etc.
-ciphers: Shows the available encoding algorithms.
As an example, specify aes256.
$ openssl ec -in ecdsa.key -out PL81Nec.key -aes256 read EC key writing EC key Enter PEM pass phrase: PL81Necpass Verifying - Enter PEM pass phrase: PL81Necpass $ ls -l total 2 -rw------- .... 314 Aug 26 14:32 PL81Nec.key -rw------- .... 302 Aug 26 13:18 ecdsa.key
*Option descriptions
ec: Elliptic curve related operations
-in filename: Specifies the elliptic curve key file name.
-out: Specifies the elliptic curve key file name with the output pathphrase.
-aes256: Use AES256 as the encoding algorithm.
You will be prompted to enter the passphrase when displaying the created private key.
$ openssl ec -in PL81Nec.key -text -noout read EC key Enter PEM pass phrase: PL81Necpass Private-Key: (256 bit) priv: b6:3c:2e:b3:37:c3:41:ca:8a:a2:68:4c:8f:dc:3d: ea:80:47:38:8d:92:b1:9a:51:71:2c:c0:f7:2c:09: 27:f2 pub: 04:7f:09:47:e9:84:6e:b8:5f:7c:85:15:36:5b:a2: 46:9e:e5:e8:04:14:1e:00:d9:d1:f4:7c:d6:9a:d9: 22:08:11:b8:fe:72:de:89:a2:53:31:91:95:40:19: 99:2a:b8:c7:0b:6b:a1:0b:47:3f:ea:59:66:cd:2c: 6f:29:87:36:ce ASN1 OID: prime256v1 NIST CURVE: P-256
Create a certificate request(CSR) from the created secret key(private key)
If the OPENSSL_CONF environment variable is not set when creating the CSR, the openssl command will fail with the message that the openssl.cnf file cannot be found.
Here, we will use a copy of the openssl.cnf file used in "SSL/TLS setup on each server (to create CSR) (Openssl)" with some changes to the Distinguished Name(DN).
Note: if you request signing for a certificate request with the same distinguished name(DN) from the same CA, the following error will occur and the request will fail.
$ openssl ca -in PL81N_C/PL81Necreq.pem Using configuration from .../openssl/nsca/openssl.cnf Enter pass phrase for .../openssl/nsca/private/cakey.pem: Check that the request matches the signature Signature ok ERROR:There is already a certificate for /C=AU/ST=Sydney/O=Pulsar Integration PL81NA Inc. /CN=www.sd.pulsarintegration.PL81N.com The matching entry has the following details Type :Valid Expires on :340814064049Z Serial Number :01 File name :unknown Subject Name :/C=AU/ST=Sydney/O=Pulsar Integration PL81NA Inc. /CN=www.sd.pulsarintegration.PL81N.com
*For information on how to reissue a certificate with the same distinguished name (DN: Distinguished Name), please refer to the OpenSSL documentation.
$ cp -p ../PL81N/openssl.cnf . $ export OPENSSL_CONF=.../openssl/nsca/PL81N_C/openssl.cnf $ openssl req -new -key PL81Nec.key -sha256 -out PL81Necreq.pem Enter pass phrase for PL81Nec.key: PL81Necpass You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]: State or Province Name (full name) [Sydney]: Locality Name (eg, city) []: Organization Name (eg, company) [Pulsar Integration PL81NA Inc.]: Organizational Unit Name (eg, section) []: www.sd.pulsarintegration.PL81Nec.com []:www.sd.pulsarintegration.PL81Nec.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: /home/mq_okada/openssl/nsca/PL81N_C: ls -l total 24 -rw------- .... 314 Aug 26 14:32 PL81Nec.key -rw-r--r-- .... 489 Aug 26 14:57 PL81Necreq.pem -rw------- .... 302 Aug 26 13:18 ecdsa.key -rw-rw-rw- .... 11147 Jul 21 19:09 openssl.cnf
*Option descriptions
req: Use this command to create, verify, and manipulate certificate requests.
-new: Generate a new certificate request.
-key filename: Specifies the filename that contains the private key used in the certificate request.
-sha256: Specify sha256 as the message digest algorithm used to sign the certificate request.
-out <filename>: File name of the output destination of the certificate request to be output.
Check the certificate request you created.
$ openssl req -in PL81Necreq.pem -text -noout Certificate Request: Data: Version: 1 (0x0) Subject: C = AU, ST = Sydney, O = Pulsar Integration PL81NA Inc., CN = www.sd.pulsarintegration.PL81Nec.com Subject Public Key Info: Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit) pub: 04:7f:09:47:e9:84:6e:b8:5f:7c:85:15:36:5b:a2: 46:9e:e5:e8:04:14:1e:00:d9:d1:f4:7c:d6:9a:d9: 22:08:11:b8:fe:72:de:89:a2:53:31:91:95:40:19: 99:2a:b8:c7:0b:6b:a1:0b:47:3f:ea:59:66:cd:2c: 6f:29:87:36:ce ASN1 OID: prime256v1 NIST CURVE: P-256 Attributes: a0:00 Signature Algorithm: ecdsa-with-SHA256 30:45:02:21:00:8e:56:af:07:50:6e:e3:76:cf:9e:8d:de:c9: 2f:13:c5:48:42:19:7d:ed:6d:fa:9a:59:85:32:6f:fe:fb:0c: 11:02:20:7d:c5:41:bf:e3:31:a5:47:e3:61:51:25:61:b9:91: 6c:d5:ed:33:6f:17:05:dd:7c:32:bd:e6:0b:8e:01:20:70
Issue a certificate at the Certificate Authority(CA) from the created certificate request(CSR)
This is the same as the procedure of "Issue a certificate at the Certificate Authority (CA) from the created certificate request (CSR)" performed for server-to-server connection and client connection, so please refer to those procedures as well.
>cd ...\openssl\winca >set PATH=%PATH%;C:\Program Files\OpenSSL-Win64\bin >set OPENSSL_CONF=...\openssl\winca\openssl.cnf >openssl ca -in ..\..\clientssl\key.csr Using configuration from ...\openssl\winca\openssl.cnf Enter pass phrase for .../openssl/winca/private/cakey.pem: winca Check that the request matches the signature Signature ok Certificate Details: Serial Number: 3 (0x3) Validity Not Before: Aug 26 07:24:50 2021 GMT Not After : Aug 24 07:24:50 2031 GMT Subject: countryName = JP stateOrProvinceName = Chiba organizationName = Pulsar Integration PL921WC Inc. commonName = www.pulsarintegration.PL921WCec.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: F8:70:D3:88:07:78:0E:6D:09:16:CB:88:7C:D3:0C:E3:C4:1B:FD:A0 X509v3 Authority Key Identifier: keyid:23:0B:5D:88:01:02:F5:6E:2B:F7:67:3D:67:A3:EF:AB:72:8D:43:A2 Certificate is to be certified until Aug 24 07:24:50 2031 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Certificate: Data: Version: 3 (0x2) Serial Number: 3 (0x3) Signature Algorithm: sha256WithRSAEncryption Issuer: C=JP, ST=Chiba, O=Pulsar Integration Inc., CN=www.pulsarintegration.com/emailAddress=support@pulsarintegration.com Validity Not Before: Aug 26 07:24:50 2021 GMT Not After : Aug 24 07:24:50 2031 GMT Subject: C=JP, ST=Chiba, O=Pulsar Integration PL921WC Inc., CN=www.pulsarintegration.PL921WCec.com Subject Public Key Info: Public Key Algorithm: id-ecPublicKey Public-Key: (521 bit) pub: 04:00:6e:40:03:ad:9c:2c:c8:13:b9:cd:12:26:02: a4:e7:3d:30:2a:c3:0f:42:db:ae:8e:3b:13:cd:fe: c2:9f:fc:07:9d:b2:f6:db:80:7d:42:ee:ce:58:7e: a1:4f:f8:fb:2e:04:9a:cb:1b:95:5b:c9:53:7a:33: 7d:1d:15:4b:11:19:ea:00:79:23:96:80:43:d2:11: 28:bc:e6:f0:0a:37:e7:12:c8:03:69:da:fb:59:67: c7:a3:81:27:11:3c:32:22:9b:80:6d:24:16:0d:db: 22:2b:67:6c:79:ee:e9:20:82:f1:60:1c:33:e0:82: 03:ab:6c:7c:82:83:c7:c5:c3:76:7e:9e:a4 ASN1 OID: secp521r1 NIST CURVE: P-521 X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: F8:70:D3:88:07:78:0E:6D:09:16:CB:88:7C:D3:0C:E3:C4:1B:FD:A0 X509v3 Authority Key Identifier: keyid:23:0B:5D:88:01:02:F5:6E:2B:F7:67:3D:67:A3:EF:AB:72:8D:43:A2 Signature Algorithm: sha256WithRSAEncryption ※CA証明書との関連でsha256WithRSAEncryptionとなる。 76:fc:9d:7e:49:bc:bb:4e:3b:0d:32:d1:57:b1:7f:c8:3c:12: 9a:d8:48:38:8b:fc:a9:e4:23:b9:a2:a9:ed:39:0f:f5:8a:76: d8:09:55:8a:9c:ea:22:42:cf:64:ab:b2:55:ae:5e:36:69:de: 3f:77:72:45:2f:85:75:1e:39:af:d8:e4:87:9f:68:65:f0:a3: 5b:ef:70:47:f7:e8:10:97:6a:3a:00:f8:75:ea:1f:6e:10:61: 81:ff:b8:03:cc:79:2e:40:4c:b4:ba:1d:af:b6:e8:14:2a:48: c2:f6:01:1c:08:79:e6:7f:d0:d5:fe:92:91:3d:16:cb:d9:f3: fc:97:b7:31:26:36:08:11:af:54:8a:34:ed:34:26:de:11:fd: 60:65:bc:1a:21:7e:48:23:dd:d3:2d:95:49:12:f3:94:28:64: cf:1b:fc:4d:cd:d1:f2:94:12:8e:9e:3e:24:8b:ab:d8:de:c8: bf:cd:fb:2e:a2:db:78:53:b0:e4:45:73:9e:41:ef:5f:1f:d6: 0b:9a:55:d5:c0:5a:ee:eb:24:e0:e3:e2:4c:22:18:79:36:25: d7:57:86:97:07:8e:38:e3:d6:f2:b4:96:34:a8:bf:99:1c:27: 1f:d7:96:01:5c:a9:1d:59:2a:bd:17:d6:b7:ee:f1:5e:d2:1e: af:97:c9:c1 -----BEGIN CERTIFICATE----- MIIDdTCCAl2gAwIBAgIBAzANBgkqhkiG9w0BAQsFADCBkTELMAkGA1UEBhMCSlAx DjAMBgNVBAgMBUNoaWJhMSAwHgYDVQQKDBdQdWxzYXIgSW50ZWdyYXRpb24gSW5j LjEiMCAGA1UEAwwZd3d3LnB1bHNhcmludGVncmF0aW9uLmNvbTEsMCoGCSqGSIb3 DQEJARYdc3VwcG9ydEBwdWxzYXJpbnRlZ3JhdGlvbi5jb20wHhcNMjEwODI2MDcy NDUwWhcNMzEwODI0MDcyNDUwWjB1MQswCQYDVQQGEwJKUDEOMAwGA1UECBMFQ2hp YmExKDAmBgNVBAoTH1B1bHNhciBJbnRlZ3JhdGlvbiBQTDkyMVdDIEluYy4xLDAq BgNVBAMTI3d3dy5wdWxzYXJpbnRlZ3JhdGlvbi5QTDkyMVdDZWMuY29tMIGbMBAG ByqGSM49AgEGBSuBBAAjA4GGAAQAbkADrZwsyBO5zRImAqTnPTAqww9C266OOxPN /sKf/AedsvbbgH1C7s5YfqFP+PsuBJrLG5VbyVN6M30dFUsRGeoAeSOWgEPSESi8 5vAKN+cSyANp2vtZZ8ejgScRPDIim4BtJBYN2yIrZ2x57ukggvFgHDPgggOrbHyC g8fFw3Z+nqSjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wg R2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBT4cNOIB3gObQkWy4h80wzj xBv9oDAfBgNVHSMEGDAWgBQjC12IAQL1biv3Zz1no++rco1DojANBgkqhkiG9w0B AQsFAAOCAQEAdvydfkm8u047DTLRV7F/yDwSmthIOIv8qeQjuaKp7TkP9Yp22AlV ipzqIkLPZKuyVa5eNmneP3dyRS+FdR45r9jkh59oZfCjW+9wR/foEJdqOgD4deof bhBhgf+4A8x5LkBMtLodr7boFCpIwvYBHAh55n/Q1f6SkT0Wy9nz/Je3MSY2CBGv VIo07TQm3hH9YGW8GiF+SCPd0y2VSRLzlChkzxv8Tc3R8pQSjp4+JIur2N7Iv837 LqLbeFOw5EVznkHvXx/WC5pV1cBa7usk4OPiTCIYeTYl11eGlweOOOPW8rSWNKi/ mRwnH9eWAVypHVkqvRfWt+7xXtIer5fJwQ== -----END CERTIFICATE----- Data Base Updated
*Option descriptions
ca: Performs basic CA functions and issues X.509 certificates and certificate revocation lists.
-in <filename>: Specify a certificate request (CSR) file.
A PEM file with the certificate serial number filename is created in the winca\newcerts directory. The issued certificate information is added to the index.txt file and the serial number in the serial file is incremented.
...\openssl\winca>dir newcerts .... 2021/08/04 15:44 4,721 01.pem 2021/08/18 15:28 4,728 02.pem 2021/08/26 16:25 3,999 03.pem .... >type index.txt V 310802064352Z 01 unknown /C=JP/ST=Chiba/O=Pulsar Integration PL92WA Inc./CN=www.pulsarintegration.PL92W.com V 310816062807Z 02 unknown /C=JP/ST=Chiba/O=Pulsar Integration PL921WC Inc./CN=www.pulsarintegration.PL921WC.com V 310824072450Z 03 unknown /C=JP/ST=Chiba/O=Pulsar Integration PL921WC Inc./CN=www.pulsarintegration.PL921WCec.com >type serial 04
Certificate verification
Please refer to the following to verify the certificate. See "Certificate Verification" for more information.
Check the symmetry of private and public keys
In the case of elliptic curves, neither Openssl nor GSKit can compare modulus(of the public key) as in the case of RSA, so only the public key is checked. Check to see the public key in the CA signed certificate(server certificate) and certificate request(CSR).
*CA signature certificate(server certificate) >openssl x509 -in newcerts\03.pem -text -noout ... Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit) pub: 04:bc:67:85:9d:83:a1:00:73:aa:81:03:7f:46:54: 02:0d:3d:81:b0:47:c4:bc:58:16:0c:0b:92:75:e2: 0c:7d:28:73:7d:63:8c:a0:11:e5:c3:bc:af:13:58: 0d:ae:19:3b:71:7c:89:69:30:63:48:9c:c3:1b:e5: 24:70:3d:19:e0 ... *Certificate request(CSR) openssl req -in ..\..\clientssl\key.csr -text -noout ... Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit) pub: 04:bc:67:85:9d:83:a1:00:73:aa:81:03:7f:46:54: 02:0d:3d:81:b0:47:c4:bc:58:16:0c:0b:92:75:e2: 0c:7d:28:73:7d:63:8c:a0:11:e5:c3:bc:af:13:58: 0d:ae:19:3b:71:7c:89:69:30:63:48:9c:c3:1b:e5: 24:70:3d:19:e0 ...
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-text: View the certificate in a readable format.
req: You can use this command to create, verify, operate certificate requests.
-in <filename>: File name to read.
-modulus: Output public key method (modulo).
-noout: Suppresses the output of the certificate in encoded form.
md5: Generate a message digest(hash value) using md5.
CA signing certificate and CA certificate subject and issuer check
Check the contents(subject and issuer) of CA-signed certificate(server certificate) and CA(root) certificate. "issuer" is the issuer of the certificate, both with the same CA Distinguished Name.
>*CA signature certificate(server certificate) >openssl x509 -subject -issuer -noout -in newcerts\03.pem subject=C = JP, ST = Chiba, O = Pulsar Integration PL921WC Inc., CN = www.pulsarintegration.PL921WCec.com issuer=C = JP, ST = Chiba, O = Pulsar Integration Inc., CN = www.pulsarintegration.com, emailAddress = support@pulsarintegration.com *CA(root) certificate >openssl x509 -subject -issuer -noout -in cacert.pem subject=C = JP, ST = Chiba, O = Pulsar Integration Inc., CN = www.pulsarintegration.com, emailAddress = support@pulsarintegration.com issuer=C = JP, ST = Chiba, O = Pulsar Integration Inc., CN = www.pulsarintegration.com, emailAddress = support@pulsarintegration.com
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-subject: Output the certificate owner name.
-issuer: Output the issuer of the certificate.
-in <filename>: File name to read.
-noout: Suppresses
Verification of intermediate CA certificate or root certificate and server certificate
>openssl verify -CAfile cacert.pem newcerts\03.pem newcerts\03.pem: OK *It should be displayed as OK
*Option descriptions
verify: Verify the validity of the X.509 certificate.
Comprehensive checks are performed on the certificates, including validation on each certificate in the certificate chain.
-CAfile <filename1>: Specify the name of the trusted certificate file.
<filename2>: Specify the file name of the CA signing certificate to be verified.
Check the contents of the server certificate
Check that the expiration date and other contents of the server certificate are as expected.
openssl x509 -noout -text -in newcerts\03.pem
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-noout: Suppresses the output of the certificate in encoded form.
-text: View the certificate in a readable format.
-in <filename>: File name to read.
Add CA(root) certificate to key repository(GSKit)
This procedure has already been performed in "Add CA(root) certificate to key repository(GSKit)" when testing server-to-server connections and client connections. If not, refer to them.
Receive personal certificate to key repository(GSKit)
This procedure is also the same as the procedure of "Receive personal certificate to key repository(GSKit)" performed for server-to-server connection and client connection, so please refer to those procedures as well.
Add a CA-signed certificate(personal certificate) to the key repository for the client machine. Importing a personal certificate must always be in the key repository that created the CSR.
Add the personal certificate using the runmqckm command.
>cd ...\clientssl >copy ..\openssl\winca\newcerts\03.pem PL921WCB.pem >runmqckm -cert -receive -file PL921WCB.pem -db key.kdb -pw PL921WCpass -format ascii 5724-H72 (C) Copyright IBM Corp. 1994, 2020. Validation successful. >
*Option descriptions
-cert: The target of the command is the certificate.
-receive: Receive certificate.
-file filename: The name of the certificate file.
-db filename: Specify the fully qualified file name of the CMS key database.
-pw password: Specify the password for the CMS key database.
-format ascii: Certificate format.
Specify Base64-encoded ASCII.
Check the CA signing certificate you added on the key repository.
runmqckm -cert -list -db key.kdb -pw PL921WCpass
runmqckm -cert -details -label PL921WCB -db key.kdb -pw PL921WCpass
Creating and deploying SSL/TLS related files(Openssl)
This work is the same as the work done for server-to-server connection, so please refer to that as well.
Place the related file created by the specified procedure in the location specified by the SSLKEYR attribute of the queue manager.
Concatenate the CA-signed server certificate and key file
Combine the CA-signed server certificate and key file into one file as follows.
In the example below, "PL81NB" is specified as CERTLABL.
$ pwd .../openssl/nsca/PL81N_C $ cp -p ../newcerts/02.pem . $ cat 02.pem PL81Nec.key > PL81NB.pem
We will also verify the combined files just in case.
$ openssl x509 -subject -issuer -noout -in PL81NB.pem subject=C = AU, ST = Sydney, O = Pulsar Integration PL81NA Inc., CN = www.sd.pulsarintegration.PL81Nec.com issuer=C = AU, ST = Sydney, O = Pulsar Integration SD Inc., CN = www.sd.pulsarintegration.com, emailAddress = support@sd.pulsarintegration.com
*Option descriptions
x509: Create, verify, and perform various other operations on X.509 certificates.
-subject: Output the certificate owner name.
-issuer: Output the issuer of the certificate.
-in <filename>: File name to read.
-noout: Suppresses the output of the certificate in encoded form.
$ openssl verify -CAfile ../cacert.pem PL81NB.pem PL81NB.pem: OK
*Option descriptions
verify: Verify the validity of the X.509 certificate.
Comprehensive checks are performed on the certificates, including validation on each certificate in the certificate chain.
-CAfile <filename1>: Specify the name of the trusted certificate file.
<filename2>: Specify the file name of the CA signing certificate to be verified.
Combine all CA certificates used for SSL/TLS communication
This has already been done for the server-to-server connection. If not, please refer to that.
Creating a path/phrase stash file
Create a pass phrase storage (stash) file using the amqrsslc command provided by MQ for HPE NonStop.
$ amqrsslc -s PL81NB Enter password for Keystore PL81NB : PL81Necpass Stashed the password in file PL81NB.sth or $ echo PL81Necpass | amqrsslc -s PL81NB Stashed the password in file PL81NB.sth $ ls -l *.sth .... 128 Aug 27 11:47 PL81NB.sth
*Option descriptions
-s : Key store path
Place created files in the SSLKey repository
Check the queue manager's SSLKEYR property for the location of the key repository.
$ mqpcf qmgr -m PL81N SSLKEYR 1: QMNAME(PL81N) SSLKEYR(.../var/mqm/qmgrs/PL81N/ssl)
*Option descriptions
qmgr: Display queue manager properties.
SSLKEYR : Show only SSLKEYR and mandatory properties
$ cp -p PL81NB.pem <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ cp -p PL81NB.sth <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ *Check the file permissions and confirm that the MQM group has R/W permissions. cd <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl/ $ chmod 666 * <MQ Install Directory>/var/mqm/qmgrs/PL81N/ssl: ls -l total 43 -rw-rw-rw- 1 MQM.MANAGER MQM 6526 Aug 10 11:10 PL81NA.pem -rw-rw-rw- 1 MQM.MANAGER MQM 128 Aug 10 13:30 PL81NA.sth -rw-rw-rw- 1 MQM.MANAGER MQM 3888 Aug 27 11:35 PL81NB.pem -rw-rw-rw- 1 MQM.MANAGER MQM 128 Aug 27 11:47 PL81NB.sth -rw-rw-rw- 1 MQM.MANAGER MQM 128 Aug 10 13:30 Stash.sth -rw-rw-rw- 1 MQM.MANAGER MQM 6526 Aug 10 11:10 cert.pem -rw-rw-rw- 1 MQM.MANAGER MQM 4400 Aug 10 11:49 trust.pem
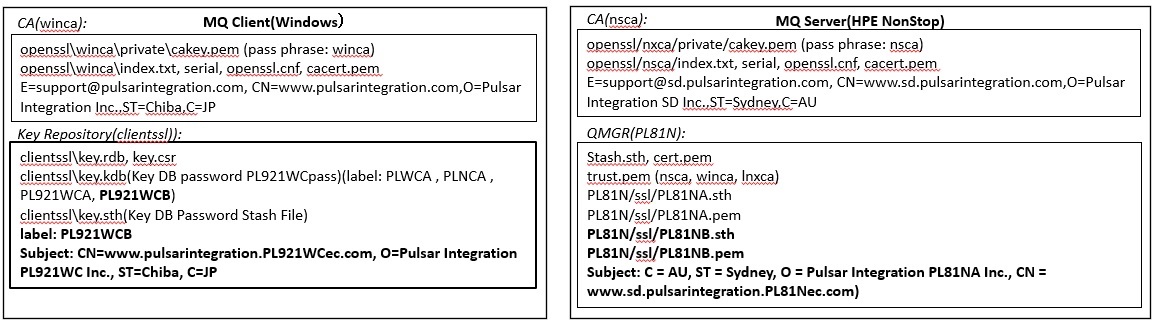
Testing a client connection using TLS(MQCD)
Try to test the connection using the channel definition structure (MQCD). For the procedure of connection test using CCDT, refer to the explanation in the previous client connection.
Creating a server-side TLS connection definition
Create a server connection channel(SVRCONN) on the server side with the following command.
$ mqpcf mqsc -qm PL81N -s "def chl(PL81N.MQICHL.EC) chltype(svrconn) certlabl(PL81NB) SSLCIPH(ECDHE_ECDSA_AES_128_CBC_SHA256)"
Ex. 13.1.1 Performing the Client Connection Using SSL/TLS(MQCD)
Specify the certificate label and CipherSpec on the MQCD. To specify the certificate label (CertificateLabel), it is necessary to use MQCD version 11(MQCD_VERSION_11) or higher. Environment variables other than MQSSLKEYR are unnecessary, so delete them. Create a client connection with specifying SSLCipherSpec and CertificateLabel by the following command.
>set MQSERVER=
>set MQCHLTAB=
>set MQCHLLIB=
>set MQSSLKEYR=C:\...\clientssl\key
>mqpgfc -qm PL81N -q LQ1 MQGMO_WAIT MQWI_UNLIMITED -x xxx.xxx.xxx.xxx(xxxx9) -ch PL81N.MQICHL.EC -cl PL921WCB -cs ECDHE_ECDSA_AES_128_CBC_SHA256 MQCD_VERSION_11
*Option descriptions
MQGMO_WAIT: Set MQGMO_WAIT in MQGMO.Options.
MQWI_UNLIMITED: Set MQGMO.WaitInterval to MQWI_UNLIMITED.
-x: Specify the connection name in MQCD.ConnectionName.
-ch: Specify the channel name in MQCD.ChannelName.
-cl: Specify the certificate label in MQCD.CertificateLabel.
-cs: Specify SSL/TLS CipherSpec in MQCD.SSLCipherSpec.
MQCD_VERSION_11: Specify MQCD_VERSION_11 for MQCD.Version.
Execute the following command on the server side and check the status of the client connection using TLS.
$ mqpcf chs -qm PL81N -c PL81N.MQICHL.EC SECPROT SSLCERTI SSLCIPH SSLPEER
1: CHANNEL(PL81N.MQICHL.EC) CHLTYPE(SVRCONN) CONNAME(xxx.xxx.xxx.xx) CHLINSTYPE(CURRENT) SECPROT(TLSV12) SSLCERTI(E=support@pulsarintegration.com,CN=www.pulsarintegration.com,O=Pulsar Integration Inc.,ST=Chiba,C=JP) SSLCIPH(ECDHE_ECDSA_AES_128_CBC_SHA256) SSLPEER(SERIALNUMBER=03,CN=www.pulsarintegration.PL921WCec.com,O=Pulsar Integration PL921WC Inc.,ST=Chiba,C=JP) STATUS(RUNNING) STOPREQ(NO) SUBSTATE(RECEIVE) RAPPLTAG(C:\...\mqpgfc.exe)
*Option descriptions
chs: Display channel status.
SECPROT: Shows the security protocol currently in use.
SSLCERTI: Shows the fully distinguished name of the remote certificate issuer(CA).
SSLCIPH: Show CipherSpec used for the connection.
SSLPEER: Shows the distinguished name of the client on the other channel.